
Entryway
What is Checkpoint Commander?
The Problem
If you own a PC or a laptop computer, or you operate one at work, the chances are that you're faced with the increasingly intractable problem of how to cope with the deluge of files you want to store on your computer. Whether you like it or not, your PC has become a digital repository, but the current lack of suitable tools and systems for managing digital information means that it's more like a digital rubbish dump.
Over the last few years there has been considerable research into the problems of managing large-scale digital repositories. The explosion in the availability of cheap processing power and storage on PCs has now brought all these problems to the individual user. Conversely, among PC users there has also been considerable experience of the very real dangers of losing your digital data for a wide variety of other reasons, which are now beginning to impact on the wider world.
The Checkpoint Solution
At the entry level all these problems can be tackled using Checkpoint Commander in stand-alone mode. However, for larger repositories, more sophisticated facilites may be needed. In this case Checkpoint Commander can act as the precursor to an extensive range of packages which together make up two Checkpoint Information Management System Suites. These are documented elsewhere.
Checkpoint Commander
Checkpoint Commander offers several methods for searching through your files, and their contents, in order to classify them into a series of 'collections' of related files, which you define. You can then build up a set of 'references' to the files in a collection - a result set. This allows you to navigate around the files, wherever they are located, on any of the storage devices attached to your computer.
Checkpoint Commander has a built-in set of internal viewers, helper applications, and facilities for linking with external helper applications as described in Plugins and helper applications. Among other things this enables you to:
- View text, image, and HTML files, and track through result sets containing them.
- Play audio files, and track through result sets containing them, including result sets saved as XSPF playlist files.
- Play video files by linking to external video players, and particularly VLC media player which can track through result sets saved as XSPF playlist files.
You can amend and re-arrange result sets, and save them for later re-use. Since a
reference to a file can be in any number of result sets, a file can be in as many
collections as you like. This provides a solution to the well-known problem of
trying to arrange files in folder trees, where you would would like to put files
into two or more distinct trees, and could otherwise only do that by replicating
files.
[NOTE] We are using the word 'collection' in a different sense
than is common. Perhaps we ought to call these things "virtual collections".
The basic method of organising files into folder trees is based on the idea of putting related files into the same folder, so that you can find them again because they are "all in the same place". This leads to the idea of putting them into some form of 'container' file. The container can then be moved from place to place within the disk storage, and access control to the files in the container can be implemented by encrypting the files with an encryption key specific to the the container. Perhaps the most well-known example of this is an encrypted "zip file". [NB. the "classic" PKZIP zip-file encryption mechanism is insecure [101].] Checkpoint Commander can be used to create and maintain a special kind of container known as a Checkpoint archive. By convention these are known as 'CPA' files. CPAs can be strongly encrypted using 256-bit AES encryption.
Checkpoint Commander allows files to be classified in many collections regardless of their physical locations. This applies even though some, or all, of the files are physically inside CPAs, and regardless of whether these CPAs are encrypted or not.
This means that users can view files, and play audio and video files both singly and using stored result sets / playlists, without unpacking them from inside encrypted CPAs. This is a strong security feature.
Checkpoint Commander also provides further security features, including secure wiping of unwanted files and the ability to securely wipe all the free space on any storage device.
Checkpoint Commander versions
Checkpoint Commander uses, and installs if it's not there already, a general-purpose framework called the Checkpoint Architecture. This framework (or core architecture) is the basis for implementing the two Checkpoint Information Management System Suites.
Two versions of Checkpoint Commander are available. Checkpoint Commander Standard is the stand-alone version; it's full-featured but does not interact with the Checkpoint suites. Checkpoint Commander Plus contains extra functionality to interface with the Checkpoint Daemon and the Checkpoint suites. The Checkpoint Commander Plus extensions have a chapter of their own in the full Checkpoint documentation. The rest of this guide applies to both versions.
Getting Started
- Windows
-
By default, the installer will have put a shortcut on your desktop; just double-click it in the usual way. The installer will even start Checkpoint Commander for you if you ask it to!
If you told it not to add the shortcut, the executable you're looking for is
cpc.exe, in thebinsubfolder of the Checkpoint installation. By default, Checkpoint is installed inC:\Program Files\Checkpoint, so the executable would beC:\Program Files\Checkpoint\bin\cpc.exe. - Linux
-
The Linux installer doesn't (yet) do desktop integration, so you have to
launch Checkpoint Commander manually. The executable you're looking for
is
/opt/cpoint/bin/cpc[Unlike Checkpoint on Windows, Checkpoint on Linux is installed in a fixed location.] If you want to add your own desktop integration, consult the handbook for your desktop / window manager (Linux has a whole bucketful).
Operating System issues
Checkpoint Commander is written in Java, which means that it will work on many different Operating Systems (OS's, also referred to as platforms). However, these OS's have differing behaviours and capabilities. This inevitably leads to platform-specific foibles. These foibles frequently depend on the family to which the given OS belongs, rather than to the individual OS. These families are as follows:
- Win9x
- Windows95 (all versions), Windows98 and '98SE, WindowsME.
- WinNT
- WindowsNT4, Windows2000, WindowsXP.
- Unix
- Linux, xBSD, Solaris, and all other Unix variants.
At this point we only support Win9x, WinNT, and Linux. We will support other operating systems when we have access to suitable testing facilities. For Apple computers, OS X support for Java 6 will also be required.
Profiles
All of Checkpoint Commander's configuration settings are stored in a profile. Everyone who uses Checkpoint Commander on a particular computer can maintain as many different profiles as they wish. For example, you might want to have one profile for sessions which are primarily about surfing around your files, and a separate one for editing, which has different viewer settings.
Each profile can be encrypted with its own password.
Profiles are stored in a profile database. Where the underlying OS supports this - WinNT and unix - every system user gets their own profile database. For those which don't - notably Win9x - everybody has to share a communal one.
To create a new profile, simply type in a new profile ID when Checkpoint Commander asks you.
Command-line arguments
Checkpoint Commander accepts some command-line arguments when you launch it: these can provide some basic automation. All are optional.
-profile <profileID>
Use the specified profile, which must exist. You will be prompted for the profile password, if required.
-arch <filepath> [<passwordFilepath>]
Open the archive which is located in the disk file specified by <filepath>. If the archive has a password, the optional <passwordFilepath> may point to the file which contains it; otherwise you will be prompted for this password. (As usual the password may be blank). NB. if you choose to record the password, this presents a security risk, which you must neutralise by some other means. For example, consider putting the password file on removable media and keeping it somewhere safe when not in use.
-jar <filepath>
Open the JAR or ZIP located in the disk file specified by <filepath>. Note that the encryption option of PKZIP is unsupported (and contraindicated, since there is an effective known-plaintext attack [101] against the encryption algorithm).
-folder <path>
On startup, move the left-hand panel to the folder specified by
<path>, as though using the Change folder option
from the Do menu. The full syntax of this is described in
Devices and Navigation.
Note that if you want to change to a non-disk device using this this method, you need to preceed this argument with the argument which opens the device.
GUI Layout
Checkpoint Commander's main view looks like this.
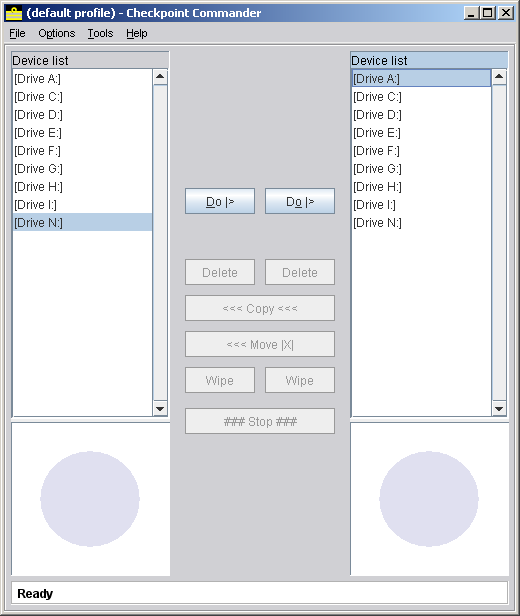
Checkpoint Commander's GUI layout
- The panels are the two tall white areas on the left and right, saying "[Drive A:]" down to "[Drive N:]".
- The previewers are the two blue-on-white circles below the panels. They provide on-the-fly preview for GIF, JPEG and PNG images. At the moment, they're not pointing to anything they can handle, hence the circle. A previewer can be resized by dragging the horizontal divider bar which separates it from the panel above.
- The panel heading is the area immediately above each panel, saying "Device List". In the screenshot one is mauve and the other grey: the mauve one represents the one which is selected. Tip: you can click a panel heading to give the corresponding panel the focus, without upsetting the selection in that panel.
- The button panel is the area between the two panels with (predictably enough!) a selection of buttons in. In this shot, most of the buttons are greyed out. The 'Do' (menu), 'Delete', and 'Wipe' buttons come in pairs; each one only applies to the panel nearest to it. The 'Copy' and 'Move' buttons act from one panel to the other; the arrows on the button indicate which way it's currently set. The panel which has the focus is the source; the other is the target.
- The status bar is the white area at the bottom, below the previewers, saying "Ready". Checkpoint Commander uses this area to tell you what's going on during operations which take a significant amount of time.

